Because Security Gives Us Freedom.
Panoptic Cyberdefense®
Managed Cybersecurity Detection
If software and hardware could prevent every security threat, there would be no intrusions, hacking, malware, or ransomware – yet we hear about new attacks almost daily. Why?
Because security is a process, not a product. The most effective cybersecurity operations require 24/7 monitoring with a Security Operations Center (SOC), separation of true security threats and information from the benign, and an immediate response. That’s why we’ve developed Panoptic Cyberdefense.
Built for Banks, Available to All
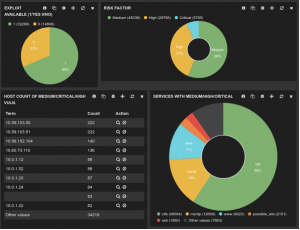 Panoptic Cyberdefense® is our SOC Managed Security service, initially built for banks in 2004 by some of the most experienced cybersecurity professionals in the industry. Our Panoptic Approach maximizes visibility throughout your network, providing you with the best defense.
Panoptic Cyberdefense® is our SOC Managed Security service, initially built for banks in 2004 by some of the most experienced cybersecurity professionals in the industry. Our Panoptic Approach maximizes visibility throughout your network, providing you with the best defense.
Panoptic Cyberdefense Goal: mitigate risk, protect sensitive data, provide visibility to upper management, elevate your security team, all while satisfying compliance requirements.
How Panoptic Cyberdefense Works
Our experts first get to know your network—inside, at the perimeter, and in the cloud—to establish baselines and thresholds and be ready for response. We tune to your policies, priorities, and procedures.
We then monitor, correlate, and alert on threats, anomalies, and compliance violations 24/7 by accepting security data from all systems in your network and in the cloud into the Panoptic SIEM®, our ELK Stack-based Security Incident & Event Manager (SIEM), both license free.
Panoptic Sensor®
The onShore Security Panoptic Sensor® is one of the most advanced network sensors in the industry with direct-driver memory access for real-time processing. It combines IDS with log, anti-malware, host detection systems, and more system correlation into one of the most advanced detection systems available. It also serves as the on-premise or virtual log collector for the cloud-based Panoptic SIEM®. Sensors can be sized with multiple 40Gb ports and multiple days of look-back PCAP storage.
The onShore Panoptic Sensor differs from most in that parallel, sensor algorithms allow for the creation of correlation rules at the sensor so that actionable events are identified before they reach the SIEM. Tuning at the sensor can be integrated with threat hunting exercises for increased gains in accuracy. All network data, security data, and log data are fed into the sensors. Some additional special sensor features include malware machine-learning detection, exfiltration detection, passive asset detection, multi-protocol sink-holing, SNMP trap capture, and syslog capture.
The Human Element
It takes people to stop people with bad intentions – you cannot rely entirely on automation. That’s why onShore Security analysts are the human component that pushes our security offering beyond simple alerting or even detection and response. By integrating with your organization, onShore analysts achieve an end-to-end view of the security of your network, and provide the high-level analysis needed for larger organizations and critical industries that must report to regulatory bodies and directors.
3 Levels of Cybersecurity Detection
Three levels of detection, response, and analysis are available:
Features:
- Flat-fee Monthly PricingNo event nor storage-based pricing. No reason to hold back on full log ingestion.
- SOC2 Type II AuditedAll of our systems, data center, and processes (service and internal) go through annual controls audits by a 3rd party. Our SOC2 report is made available under NDA.
- Panoptic SIEM®, ELK Stack-Based, license-freeThe Panoptic ELK Stack-based SIEM is our advanced, purpose-built SIEM for analyzing and reporting security data.
- Panoptic Sensor® IDS, license-freeAlways deployed in HA pairs, bare-iron or VM, the onShore Security Panoptic Sensor® is one of the most advanced IDS network sensors in the industry, with direct-driver memory access for real-time processing. Basic version excludes full packet capture.
- 24/7 Threat-Level Alerting EverywhereDetect on-premise, in the cloud, on virtual workloads, even SaaS applications.
- Threat, Anomaly, and Compliance DetectionDetection isn't just monitoring for automated alerts.
- Log and Event CorrelationCorrelation rules are built across disparate data.
- Analyze Any Log, End-point Protection, SNMP, or API DataWe can customize parsers for almost any log or output source.
- Network-level Ingestion and CorrelationSNMP, device health, port changes, traffic metrics, and netflow data help with anomaly detection.
- CVE Scan Ingestion and CorrelationCVE scan correlation allows for risk-aligned detection.
- 12-Month SIEM, Log, and Incident Off-Site RetentionAll log, session, alert, and ticket data are retained off-site for 12 months by default.
- Proprietary Signature UpdatesOur own 15-year signature set is updated continuously.
- Banking Signature UpdatesWe maintain banking-specific signature sets.
- Community Signature UpdatesWe collaborate with the cybersecurity community.
- SIEM ReportsSIEM reports aggregate the alerts and correlated security data and deliver it to you in an easily understood and communicated format.
- Firewall ReportWe provide reporting for blocked and filtered content, threat detection, geo-activity, and bandwidth graphing.
- Panoptic Sensor® Full Packet Capture IDSUp to 2 days of lookback session data. Sensors always come in HA pairs and are connected to switch span ports.
- Multiple 40G PortsMultiple network segments can connect to a single sensor HA pair. Packet aggregators can be used in larger networks where span ports can be overwhelmed.
- Ingress, Egress, Lateral, and Virtual Network SegmentsNo traffic is missed so APTs are thwarted early in the kill-chain.
- Network Anti-malwareMalware detection at the network level provides valuable security data and adds an additional layer to endpoint detection.
- Network Behavior AnalysisDeeper knowledge provides useful insights and reduces false-positives.
- Host ProfilingHosts are tracked and mapped against DHCP for historical profiling. Producer/consumer ratios and micro-segmentation triggers are tracked for anomaly and exfiltration detection.
- DNS Sinkholing and OrchestrationIntegration with NexGen firewalls allows blacklisted traffic to be analyzed.
- Shared-key DecryptionHosts with ingress traffic can share keys for full passive https decryption and detection.
- Primary Security AnalystYour analyst knows you and your network.
- Proactive Threat HuntingSecurity engineers mine your network data, investigating anomalies.
- Incident ResponseWe take defensive action 24hrs/day.
- Inform Security PolicyDetection checks for compliance to close the loop on policy development.
- 12-Month SIEM, Log, Incident, and Tagged PCAP Off-Site RetentionAll log, session, alert, tagged full packets and ticket data are retained off-site for and upgraded 12-months.
- Security OrchestrationWe provide assistance in bringing together all cybersecurity efforts.
- Monthly Security BriefingThis briefing provides an understanding of the activity and its relevance.
- Threat Landscape ReportingIndustry and individual threats are curated and reported on in our briefings.
- Credential Exposure ReportingDarkweb scans are preformed for credential eposure and reported on in our briefings.
- Board Reporting and PresentationDirectors and upper management gain confidence on cybersecurity posture.
- Reporting to IT CommitteeAs needed additional reporting and analysis.

MDRonShore’s Panoptic MDR cybersecurity service includes alerting, analysis, and response for detected events without the cost or hassle of operating your own SIEM or SOC.

MDR + NDRonShore’s Panoptic MDR + MDR cybersecurity service includes alerting, analysis, and response for detected events and adds full packet capture IDS, advanced sensor functions, and a dedicated Security Analyst.

Security OrchestrationonShore Security's Security Orchestration adds a monthly security briefing and report with high-level summary data on events and activity as well as on the threat landscape.